How to Recognze That a Solution Will Use a Stack
Managing your cybersecurity solutions portfolio requires a measured approach, lest you develop a bloated solutions stack and even worse for MSPs, margin squeeze. Following a proven security framework can help you set the right course.
 When I started my company in 2008, the MSP market focused on a core solutions stack that included remote management and monitoring (RMM), antivirus, antimalware, antispyware (remember spyware programs?) and antispam. Business continuity and disaster recovery (BCDR) solutions were the new kids on the block, vying for a position in our standard stacks. These were the non-negotiables and became part of what all our managed clients received.
When I started my company in 2008, the MSP market focused on a core solutions stack that included remote management and monitoring (RMM), antivirus, antimalware, antispyware (remember spyware programs?) and antispam. Business continuity and disaster recovery (BCDR) solutions were the new kids on the block, vying for a position in our standard stacks. These were the non-negotiables and became part of what all our managed clients received.
As time went on, our stack evolved, especially around cybersecurity, particularly because there was so much innovation occurring in that space. Anyone who knows me knows I like the shiny new thing. Coming out of corporate IT for a financial services firm and helping independent investment firms, I enjoy vetting new emerging solutions and introducing them to clients, which serves a twofold purpose. First, customers are better protected. Second, they come to know us as trusted business partners. Even if a solution was more intended for enterprise companies, we found a way push the square peg in the round hole anyway—and make it a success.
The problem with this approach is it can create a bloated solutions stack and even worse for MSPs, margin squeeze. Admittedly, we didn't do a good job of monetizing changes to our portfolio and needed to find a better way to evaluate what products made it to our standard stack and what we could provide as premium add-ons. We dove headfirst into security frameworks such as NIST-CSF (Cyber Security Framework), Center for Information Security 20 (CIS20), now the CIS18, Mitre's ATT&CK framework, the Australian Signals Directorate Essentials 8, and others. These frameworks provide a blueprint for governing security programs and help determine an MSP's minimal viable security stack. Newer versions of these frameworks also identify a maturity model through implementation levels.
Identify, Protect, Defend, Respond and Recover
A great place to start are the five NIST-CSF functions, which serve as the basis for the CompTIA Security Trustmark+: Identify, Protect, Defend, Respond, and Recover. The framework details policies, procedures, and operations necessary for each function. What solutions do you need to help fulfill these functions? Some are products you buy; some are services you contract or develop; and others will be processes and procedures that your team puts into motion.
In addition, some are proactive, and some are reactive; the more reactive, the more resources are needed, whether on your team or you work with a third party. Your vendor partners should be able to tell you how they fit into this framework to help you plan. Some vendors may clearly fit into one bucket, while others reside in multiple buckets. If they can't articulate that level of detail to you, it may be worth looking for a new partner that can. The list below is not exhaustive but can be used as a guideline to get started updating your cyber stack to meet current needs (click on the image to open a PDF). I'm going to focus on products and services in this area, but equally if not more critical are policies and procedures:
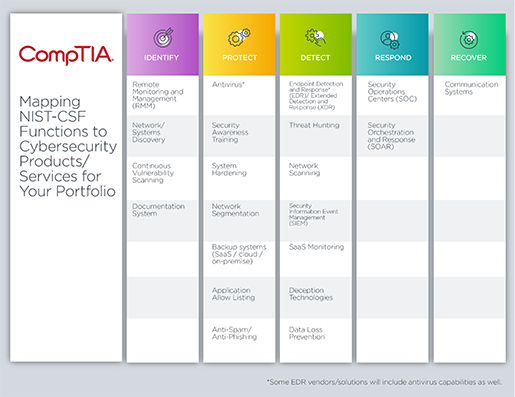
As you examine your skills and requirements across each of the five functions, fewer solutions will directly "check the box," and you must leverage people and documented processes to help complete your stack. I usually follow the Tony Hsieh model of "don't outsource your core competency," but that doesn't mean you shouldn't utilize other companies' support for things outside your expertise or if something is cost-prohibitive to implement (such as a SOC). It also doesn't mean you have to stay that way forever. Partnering may be an excellent way to test the market. However, it may be more cost-effective to leverage the capabilities of a security provider to help round out your team.
In the end, focus on the process, identify the needs for your clients/verticals to determine which controls you will need to tackle first and build the policy for that control. You may determine that a tool isn't needed and just building a policy and procedures that follow it may be enough. However, investing in solutions and partners that will save you time is worth the look.
Raffi Jamgotchian is the founder and CTO of Triada Networks , vice-chair of CompTIA's Cybersecurity Community , and a member of the CompTIA ISAO SME Champions Council .
Join CompTIA's Cybersecurity Community
for more information and conversation about protecting your clients .
How to Recognze That a Solution Will Use a Stack
Source: https://connect.comptia.org/blog/plan-your-cybersecurity-stack-for-2022
0 Response to "How to Recognze That a Solution Will Use a Stack"
Post a Comment