Allows Direct Commputer-to-computer Communication Using Ipv6
Protocol Definition: It is a digital language through which we communicate with others on the Internet. protocol meaning is that it a set of mutually accepted and implemented rules at both ends of the communications channel for the proper exchange of information. By adopting these rules, two devices can communicate with each other and can interchange information. We can't even think of using the Internet without Protocols. Each protocol is defined in different terms and different use with unique name. Message travel from sender to receiver via a medium (The medium is the physical path over which a message travels) using a protocol.
'Protocols' are developed by industry wide organizations. All data of protocols are stored in binary information. Protocol language is a mixture of bits, characters, integers, etc.
Each of it has its own access method of exchanging data over a computer network, such as LAN, Internet, Intranet, etc. One of the most common and known protocol example is HTTP, that is used over the world wide web. there are different protocols used in internet that are
• TCP/IP (Transmission Control Protocol/Internet Protocol)
• ARP (Address Resolution Protocol)
• DHCP (Dynamic Host Configuration Protocol)
• DNS (Domain Name System)
• FTP (File Transfer Protocol)
HTTP is an application-layer protocol that is used for transferring files on the internet. It is used by web browsers and servers use to communicate.
There are different types of protocols and different uses of protocol.
We'll be covering the following topics in this tutorial:
Types of Protocols
A protocol technologies is required for communication between computers. To connect different types of computers from a variety of computer vendors, protocols must be first standardized. The ARPA (Advanced Research Project Agency) part of the US Defense program was the first to introduce the concept of a standardized protocol. ARPA is a resource sharing network connecting different computers at universities and laboratories in the US. The concept of the protocol and its layer structure, emerged from the ARPA network. ARPA developed an integrated network using packet protocol and is also renowned for its development of packet switching.
TCP
Transmission control protocol is used for communication over a network. In TCP data is broken down into small packets and then sent to the destination. However, IP is making sure packets are transmitted to the right address.
Internet Protocol (IP)
IP is also working with TCP. It is an addressing Protocol. IP addresses packets route them and show different nodes and network Unless it reaches its right destination. The IP protocol is developed in 1970.
FTP
File transfer protocol is basically used for transferring files to different networks. There may be a mass of files such as text files, multimedia files, etc. This way of file transfer is quicker than other methods.
SMTP
Simple mail transfer protocol manages the transmission and outgoing mail over the internet.
HTTP
HTTP is based on client and server model. HTTP is used for making a connection between the web client and web server. HTTP shows information in web pages.
Ethernet
Ethernet is a most important for LAN communication. Ethernet transmits the data in digital packets. If any computer wants to use this protocol they should contain Ethernet Network Interface Card (NIC). The card is implemented with unique address code fixed in the microchip.
Telnet
Telnet is an established with some rules which are used to connect to another computer. Telnet is mainly used for the remote login process. The computer which is requesting for a connection that is a local computer and which is accepting the connection that is a remote computer. If you give a command in a local computer that command is executed in the remote computer. Telnet is also based on client and server model.
Gopher
Gopher is an application layer protocol, which is used for searching and retrieving documents from remote sites. This is possible to start an online connection with other computers through gopher.
Transmission Control Procedure
As important as it is that there should be one accepted standard that allows all types of machines to communicate. There are several different protocols in use today. These are:
• Synchronous Protocol These protocol involve timing information of sender along with the data bytes. This protocol helps receiver to remain synchronization with the sender. When the sender has no data to transmit, the sender transmits a sequence of alternating 0s sand 1s to maintain sender/receiver synchronization. This sequence of 0s and 1s is called idle flags. Data bytes are packaged into small chunks called packets including address fields and check-sums. As error checking is an inherent feature of this protocol, this overcomes the major deficiency of the asynchronous protocol.
• Asynchronous Data Link Control (DLC) Protocols Asynchronous protocols are used primarily for low-speed data communications between PCs and very small computers. Framing occurs at the byte level, with each byte surrounded by a start bit (a 0 bit) and a stop bit (a 1 bit). A parity bit often accompanies each character as well.
Character-orientated Protocols (COP)
Each character has its own meaning in character-orientated protocols. A character may be a data byte or a control byte during transmission. The main COP in use today is known as Bisync or binary synchronous. Each character sent is transmitted using the ASCII code. Control bytes obviously have values in ASCII of between 00 and 1F, whereas data bytes have values between 20 and 7F.
In this type of scheme, following Figure represents a sequence of communication between the sender and receiver. This can be inferred as handshaking between the sender and receiver:
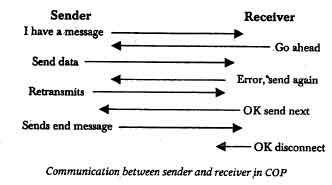
This has an acknowledgement scheme. In this case, if an acknowledgement is not received by the sender in a specified time, the sender retransmits the packet. This time is called time out. After the successful transmission of a packet, next packets are transmitted until entire message is sent. If a packet is received and contains errors, the receiver will send a negative acknowledge. This implies that the sender has to send it again. Data bytes contain data according to the ASCII code for text or simply a value between 0 and 255 for binary data. Control bytes determine the behavior of the communication link, and are used for a range of different purposes.
The link between sender and receiver is half duplex.
• Binary Synchronous Protocol (Bisync or BSC) Bisync was developed by IBM in 1966 as a character-oriented protocol that frames the data with control codes which apply to the entire set of data. Bisync organizes data into block of up to 512 characters, which are sent over the link sequentially (one-at-a-time) as shown in Figure. An ACK or NAK is transmitted from the receiving terminal to the transmitting device following the receipt of each block Error control is on the basis of a Block Checking Character (BCC) that is transmitted along with the data. The receiving device independently calculates the BCC and compares the two calculations.
From the Figure, it can be seen that each message has three parts:
• Header: This is recognized by the control characters SOH (Start of Header)
• Text:This is recognized by the control characters STX (Start of Text block)
• Trailer: This is recognized by the control characters ETX (End of Text block)
SYN characters are used to establish synchronization between the sender and receiver. The message block follows the SYN characters.
In this scheme, sender breaks each message into blocks of small messages for transmission. The trailer for each block consists of a block check character (BCC). Both the sender and the receiver generate distinct BCC during the transmission of message. At the end of receiving the trailer, the receiver compares its own BCC against that of the senders. If they are the same, this indicates the block has been successfully received without any error. In this case, the receiver will reply using a positive acknowledge (ACK). If the BCC of the receiver does not match that of the sender, the receiver knows an error has occurred during transmission, and will instruct the sender to retransmit the block by replying with a negative acknowledge (NACK). This is also explained with the help of Figure.
Bisync scheme has one major disadvantage in distinguishing between the control characters and the same text in a binary file. If a control character like ETX occurs in the text field, the receiver would interpret this as the end of the text field and take the next character as the BCC. This is incorrect. This is overcome by using a technique called data transparency. This means preceding each control character with the Data link Escape control character (DLE). If the receiver gets a DLE code, it knows the next byte is a control code. The receiver discards the DLE control character. What happens if the sender has a DLE code as part of the text block? In this case the sender precedes it with a DLE, and the receiver discards the first and uses the second as a data byte.
Allows Direct Commputer-to-computer Communication Using Ipv6
Source: https://ecomputernotes.com/computernetworkingnotes/computer-network/protocol
0 Response to "Allows Direct Commputer-to-computer Communication Using Ipv6"
Post a Comment